Business disaster recovery planning is the structured approach an organization uses to resume operations after an unplanned incident. This is not just an IT checklist; it is a critical business function that protects revenue, reputation, and long-term viability against disruptions ranging from ransomware attacks to catastrophic weather events.
A robust plan enables a coordinated, effective response the moment a crisis occurs, minimizing financial and operational impact.
Why a Disaster Recovery Plan Is a Business Imperative
For underwriters, brokers, and risk managers, an organization's disaster recovery plan—or lack thereof—is a direct indicator of its operational resilience. It is a tangible measure of how well a business can withstand a significant disruption. Neglecting this function exposes a company to severe financial and reputational damage that can rapidly escalate.
Even a minor disruption can cascade into a significant operational failure.
Consider a regional insurance brokerage that loses access to its core CRM for 48 hours due to a localized power grid failure. This is not merely an inconvenience; it is a complete halt to its ability to generate quotes, process claims, or communicate with policyholders. The immediate revenue loss is damaging, but the erosion of client trust and market reputation can have lasting consequences.
The Quantifiable Cost of Downtime
When operations cease, the financial impact is immediate and significant. Research indicates that 100% of organizations report revenue loss resulting from IT downtime. On average, companies experience 86 outages annually, with a staggering 55% occurring weekly. These figures underscore why a structured recovery framework is a non-negotiable component of modern risk management.
Beyond direct revenue loss, secondary costs accumulate quickly:
- Regulatory Fines: Failure to protect data or maintain service availability can trigger substantial penalties, particularly in regulated sectors like finance and healthcare.
- Contractual Penalties: Breaching Service Level Agreements (SLAs) with clients or partners can result in costly financial penalties and legal disputes.
- Brand Erosion: Every hour of system downtime erodes customer confidence, damaging a market reputation that is difficult and expensive to rebuild.
For any risk professional, the absence of a tested disaster recovery plan should be a material red flag. It signals a reactive approach to risk management, which directly influences underwriting decisions, premium calculations, and insurability.
A modern disaster recovery plan is built on several key pillars. The following table provides a concise overview of the core components.
Core Components of a Modern Disaster Recovery Plan
| Component | Objective | Key Metric |
|---|---|---|
| Risk Assessment | Identify and quantify potential threats to business operations. | Threat Likelihood & Impact Score |
| Business Impact Analysis (BIA) | Determine the financial and operational impact of disruptions. | Recovery Time Objective (RTO) |
| Recovery Strategy | Define the methods for restoring IT systems and business functions. | Recovery Point Objective (RPO) |
| Plan Documentation | Create clear, actionable guides for response and recovery teams. | Plan Accessibility & Clarity Score |
| Testing & Maintenance | Regularly validate the plan's effectiveness and keep it updated. | Mean Time to Recovery (MTTR) |
Each of these components is essential for constructing a plan that is effective under real-world crisis conditions.
A Non-Negotiable Part of Modern Risk Management
Ultimately, a disaster recovery plan is a cornerstone of responsible corporate governance that extends beyond IT restoration. By adhering to frameworks like HITRUST, businesses demonstrate compliance and robust risk management, making a DRP a non-negotiable imperative.
For an underwriter evaluating a client's risk profile, a well-documented and frequently tested plan provides tangible proof of resilience. This proactive posture not only reduces claim likelihood but also positions the business as a more favorable risk. Our guide on **disaster preparedness for businesses** offers additional insights on building this operational strength.
In today's volatile risk landscape, a proactive recovery strategy is not an optional expense—it is a core investment in business survival.
Conducting a Business Impact Analysis

Image
Before constructing a defense, you must understand what you are defending. A Business Impact Analysis (BIA) is the diagnostic process that quantifies how a disruption to any single business function would ripple across the entire organization, impacting revenue, operations, and reputation.
For risk professionals, the BIA is the foundational data layer for any credible business disaster recovery planning. It provides the empirical evidence needed to justify investments and allocate resources strategically. Without a BIA, a recovery plan is based on assumption, not analysis.
Mapping Your Mission-Critical Functions
The first step is to identify functions essential for the organization's survival. This involves pinpointing the operational pillars that generate revenue, serve clients, or fulfill mandatory regulatory obligations.
Focus on core processes, not just IT systems. For an insurance carrier, this list would include:
- Claims Processing: The ability to intake, assess, and pay claims is the operational lifeblood of the business.
- Policy Underwriting and Issuance: This function generates new revenue and manages the firm’s aggregate risk portfolio.
- Customer Relationship Management (CRM): Without access to client data and policy details, service delivery stops and client retention is jeopardized.
- Financial Reporting: The capacity to manage financial transactions and meet regulatory reporting deadlines is non-negotiable.
Once these pillars are identified, you must map their dependencies, including specific applications, data sets, key personnel, and third-party vendors. This detailed mapping uncovers hidden vulnerabilities and single points of failure.
Calculating the True Cost of Downtime
With critical functions mapped, the next step is to calculate the tangible and intangible costs of an outage for each. This financial modeling is crucial for securing executive buy-in. An underwriter who can state, "A 48-hour outage of our CRM will cost $500,000 in direct revenue and trigger a 15% spike in customer churn," presents a far more compelling case for recovery funding.
To derive these figures, analyze the impact over incremental time periods—one hour, eight hours, 24 hours, and beyond. This demonstrates how damage accelerates over time, providing essential context for setting recovery objectives. For a deeper analysis, our article on **business interruption insurance coverage** offers valuable perspectives.
A BIA translates operational disruptions into the language of the C-suite: financial impact and risk exposure. It is the most effective tool for demonstrating the ROI of resilience and repositioning disaster recovery from a cost center to a strategic investment.
Setting Realistic Recovery Objectives
The data from your BIA directly informs the two most critical metrics in your disaster recovery plan: the Recovery Time Objective (RTO) and the Recovery Point Objective (RPO).
- Recovery Time Objective (RTO): This is the maximum acceptable duration a system or function can be offline before the business impact becomes unacceptable. A critical claims processing application might have an RTO of four hours, while a less vital internal reporting tool could have an RTO of 48 hours.
- Recovery Point Objective (RPO): This defines the maximum acceptable amount of data loss, measured in time. An RPO of 15 minutes for a transactional database indicates the business can tolerate losing, at most, the last 15 minutes of data entered before the disruption.
These metrics are the direct output of your impact analysis. The RTO is dictated by how quickly financial and operational damage becomes intolerable, while the RPO is determined by the organization's tolerance for data loss. Defining these precisely provides your recovery strategies with clear targets, ensuring technical solutions are aligned with business requirements.
Identifying and Prioritizing Business Risks

Image
An effective business disaster recovery planning framework is proactive, not reactive. Building a resilient organization begins with a structured, comprehensive assessment of potential threats. This process extends beyond obvious hazards to create a full-spectrum view of potential disruptions, from natural disasters and technological failures to human error.
Effective risk identification is a systematic process of mapping threats directly to business operations. For professionals in the insurance and risk management sectors, this means connecting a potential event to a specific business outcome. For example, how might a regional flood not only trigger a surge in claims but also disable the data center required to process them?
Expanding the Threat Landscape
Many organizations focus on a narrow band of well-known risks, such as fire or cyberattacks, while ignoring less obvious threats that can be equally damaging. A thorough risk assessment must categorize and examine a wider array of potential disruptions.
This expanded view should include:
- Natural Disasters: Analyze beyond direct physical impact. Events like floods, wildfires, and hurricanes create significant secondary disruptions, including infrastructure collapse and employee displacement, which can cripple a business.
- Technological Failures: This broad category covers hardware malfunctions, software bugs, and widespread outages from cloud service providers that can halt operations.
- Human-Caused Events: This includes malicious acts like ransomware and insider threats, as well as unintentional errors such as the deletion of critical data or system misconfiguration.
- Supply Chain and Vendor Disruptions: The failure of a critical third-party provider, whether a data processor or a logistics partner, can impact a business as severely as an internal disaster.
For an underwriter evaluating a portfolio of commercial properties, this perspective is crucial. A hurricane is not just a threat to a single building; it is a risk to the regional power grid, local infrastructure, and every supply chain supporting the businesses in its path.
Using a Risk Assessment Matrix
Once you have a comprehensive list of potential threats, the next step is prioritization. A risk assessment matrix is a practical tool for scoring and ranking threats based on two key dimensions: likelihood and impact.
- Likelihood: What is the probability of this event occurring within a given timeframe (e.g., the next 12-24 months)? This can be rated on a scale from "rare" to "almost certain."
- Impact: If this event occurred, how severe would the consequences be? This assesses financial loss, reputational damage, and operational disruption, often rated from "negligible" to "catastrophic."
Plotting each risk on this matrix creates a clear visual hierarchy for resource allocation. A high-impact, high-likelihood event, such as a targeted ransomware attack, demands an immediate and robust response. A low-impact, low-likelihood event can be placed on a watch list with less intensive controls.
A risk matrix transforms a qualitative list of concerns into a data-driven action plan. It compels decision-makers to focus finite resources on the threats that pose the greatest existential danger, ensuring recovery efforts deliver maximum value.
This structured approach is also the most effective tool for justifying investments in a disaster recovery program. It is far more compelling to present a budget request based on mitigating a "high-probability, catastrophic-impact" cyber threat than to ask for funds for "better security." This process is the strategic core of effective business disaster recovery planning.
Alarmingly, many organizations struggle with this foundational step. Research on business continuity management reveals that only 39% of businesses with mature frameworks can restore critical operations within their target times. Data also shows that only 30% of all businesses have a clearly defined plan, leading to significant failures during outages. You can review more insights in these disaster recovery planning statistics. This highlights the critical gap between acknowledging risk and achieving operational readiness.
Developing Your Disaster Recovery Strategies
With risks assessed and the financial impact of downtime quantified, the next phase is to translate analysis into a functional defense: your recovery strategies.
This is where planning transitions from theory to execution. The objective is to select the specific tools, technologies, and procedures that will restore operations within your defined RTOs and RPOs. This involves building layered defenses for infrastructure, personnel, and communications, balancing recovery speed against budgetary realities.
Selecting the Right Recovery Infrastructure
For most organizations, the core of disaster recovery is restoring IT systems. The traditional approach involves establishing a secondary physical location, or recovery site. These sites typically fall into three categories, each with distinct cost and recovery speed profiles.
- Hot Sites: A hot site is a fully operational mirror of the primary data center, running in real-time synchronization. It is equipped for immediate failover, enabling an RTO measured in minutes. This is the gold standard for speed but is also the most expensive option, as it requires duplicating all critical infrastructure.
- Warm Sites: A warm site is a compromise between cost and speed. It has hardware and network connections in place but does not run a real-time mirror of production systems. Recovery requires loading the most recent data backups. The RTO is typically measured in hours to a day, providing a balanced solution for many applications.
- Cold Sites: A cold site is the most basic and least expensive option, providing only a facility with power, cooling, and network connectivity. In a disaster, the organization is responsible for transporting and installing all necessary equipment. The RTO can be days or weeks, making this suitable only for non-critical systems with a high tolerance for downtime.
A tiered approach is often the most cost-effective strategy. A financial institution might use a hot site for its critical payment processing systems (RTO < 15 minutes) while using a warm site for internal HR applications that can tolerate a 24-hour outage.
This table breaks down the three primary recovery site options to help align operational requirements with budget constraints.
Comparison of Disaster Recovery Site Options
| Site Type | Recovery Speed (RTO) | Cost | Best For |
|---|---|---|---|
| Hot Site | Minutes | Very High | Mission-critical systems with zero tolerance for downtime (e.g., e-commerce, financial transactions). |
| Warm Site | Hours to a Day | Moderate | Important business functions that can tolerate a few hours of downtime (e.g., internal email, CRM). |
| Cold Site | Days to Weeks | Low | Non-essential functions with a very high tolerance for downtime (e.g., development servers, archives). |
Choosing the right combination of these sites is a strategic decision that directly impacts both resilience and capital expenditure.
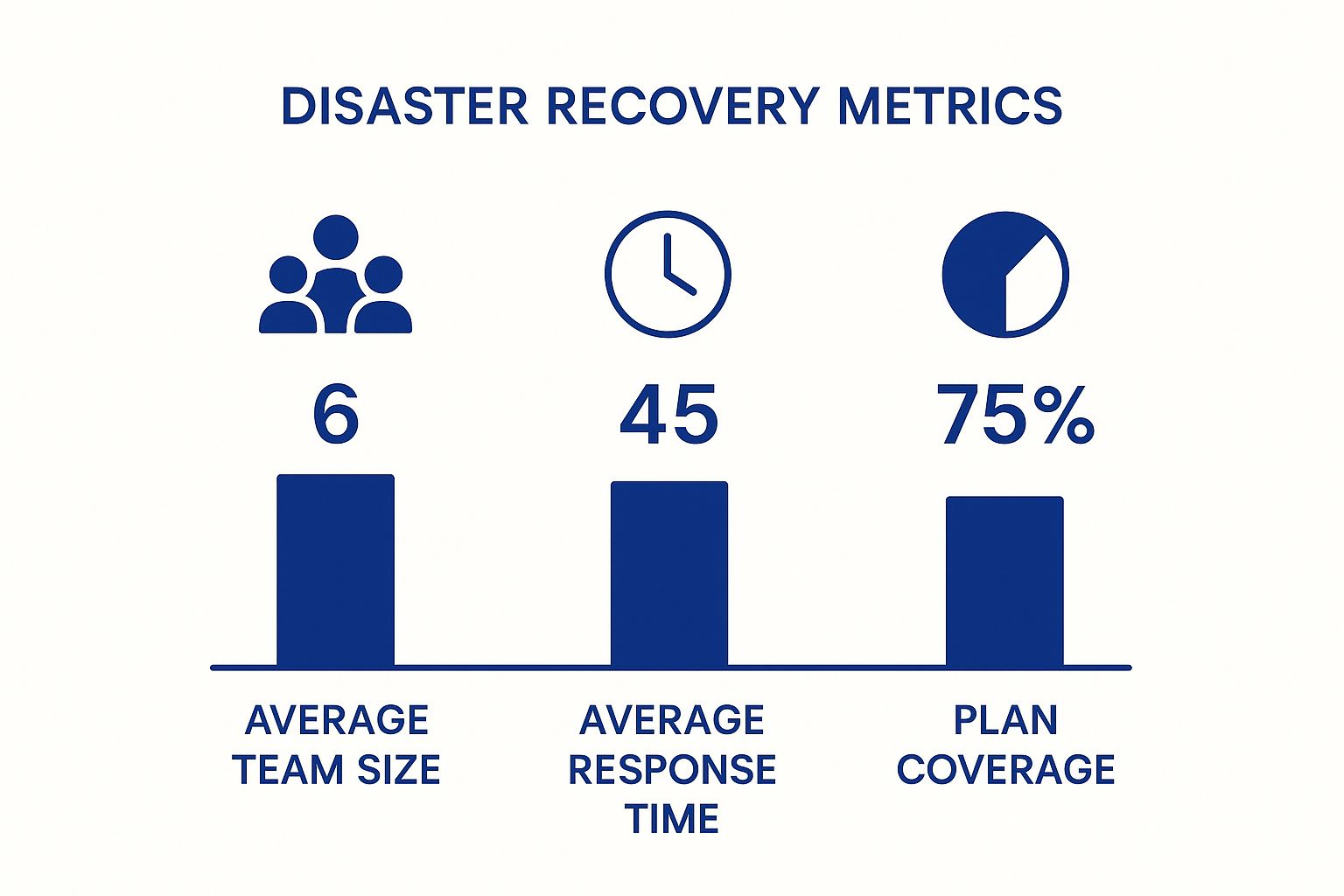
Image
As the data shows, allocating sufficient resources to recovery teams often correlates with faster response times and better outcomes. This underscores the importance of properly staffing disaster recovery efforts.
Cloud and Hybrid Recovery Models
Cloud-based disaster recovery, or Disaster Recovery as a Service (DRaaS), has fundamentally altered the strategic landscape. The cloud offers significant flexibility, allowing organizations to maintain a "pilot light" environment—a minimal version of their systems—that runs at a low cost and can be scaled to full production capacity in minutes during a disaster.
This approach dramatically reduces the capital expenditure required for maintaining duplicate physical hardware.
A hybrid model combines the benefits of on-premises infrastructure and cloud services. An insurance company, for example, might keep its primary applications in its own data center for performance control but use a cloud provider for continuous replication of its critical databases. If the primary site fails, they can failover to the cloud database and reroute traffic, achieving an RTO of under 15 minutes without the expense of a dedicated hot site.
Ensuring Workforce Continuity
A commonly overlooked vulnerability is workforce accessibility. An infrastructure can be fully recoverable, but it is operationally useless if employees cannot access it. A disaster recovery strategy must account for scenarios where a flood, wildfire, or extended power outage prevents personnel from reaching the office.
The plan must include provisions for your people:
- Remote Work Protocols: Secure VPN access, company-issued laptops for key staff, and cloud-based collaboration tools are essential for enabling work from any location.
- Alternate Work Locations: Designate secondary office spaces or establish agreements with co-working facilities outside the primary location's potential impact zone.
- Communication Plans: An emergency notification system capable of reaching all employees via text, email, and phone is critical for disseminating information and instructions.
Reviewing business continuity plan examples can provide a practical framework. Analyzing how other organizations have structured their plans can offer valuable insights and adaptable templates for your specific needs.
Building and Communicating Your Recovery Plan
A detailed recovery strategy is ineffective if it is not documented in an actionable plan. Many organizations fail at this stage, translating high-level strategy into a clear, usable guide. For underwriters and risk managers, the quality of this documentation is a direct indicator of an organization's true preparedness.
An effective plan is not a lengthy treatise; it is a concise playbook designed for use under extreme pressure. Its primary function is to eliminate ambiguity during a crisis, ensuring a coordinated and decisive response rather than a chaotic one. It serves as the single source of truth for the entire response effort.
Core Components of an Actionable Plan
A functional business disaster recovery planning document is a comprehensive guide that orchestrates the actions of people, processes, and technology. To be effective, every plan must clearly define several key components.
A minimal plan must include:
- Activation Criteria: Define the specific events or thresholds that trigger the plan. This eliminates guesswork and empowers the team to act decisively without waiting for hierarchical approvals.
- Response Team Roster: Clearly identify recovery team members by name, role, and specific responsibilities, including multiple methods of contact for each individual.
- Step-by-Step Procedures: Provide clear, sequential instructions for failing over systems, restoring critical data, and bringing operations back online.
- Vendor and Partner Contacts: List all critical third-party suppliers with their emergency contact information and relevant service-level agreements.
This structure ensures that any response team member can immediately understand their role and the required actions, even if key leadership is unavailable.
A well-documented plan is the bridge between strategy and execution. It is evidence that a business has progressed from theoretical resilience to operational readiness. For an insurer, this is a critical differentiator when assessing risk.
Establishing Communication Protocols
During a disaster, effective communication is as critical as technical recovery. The plan must include a dedicated section that maps out how, when, and what to communicate to all stakeholder groups. A pre-defined project communications plan template adapted for a crisis is essential for any recovery effort.
This section of the plan defines the communication hierarchy and the channels for disseminating information.
- Employees: How will staff be notified of the incident, office closures, or remote work protocols?
- Clients and Customers: What is the messaging strategy to maintain trust and manage expectations?
- Insurers and Legal Teams: Who is the designated point of contact for officially notifying the insurance carrier and legal counsel?
A pre-approved communication tree ensures all messaging remains consistent, accurate, and timely. Our guide on **crisis communication best practices** offers valuable frameworks for this. By documenting these protocols in advance, an organization can ensure it speaks with a single, confident voice under duress, protecting its reputation when it is most vulnerable.
Testing and Maintaining Your Disaster recovery plan

Image
A disaster recovery plan is a living document, not a static artifact. If it is not validated regularly, it is based on hope, not evidence.
From an underwriter's perspective, a rigorous testing schedule is often more indicative of preparedness than the plan itself. Testing demonstrates a tangible commitment to resilience, moving beyond a mere compliance checkbox.
Without regular validation, a plan is merely a set of unproven assumptions. The cycle of testing, learning, and refining separates a resilient organization from one with a plan on paper. The objective is to identify gaps before a real crisis does.
Conducting Meaningful Plan Tests
Testing your business disaster recovery planning is an exercise in discovery, not a pass/fail assessment. Different testing methods uncover different weaknesses, so a blended approach is most effective.
Common and effective methods include:
- Tabletop Exercises: A guided walkthrough where the recovery team discusses a specific disaster scenario step-by-step. This low-cost, non-disruptive method is excellent for identifying flaws in communication plans and clarifying roles.
- Walkthroughs: A more involved test where team members execute their assigned recovery tasks without activating the full recovery environment. This can uncover issues like expired credentials, access problems, or outdated procedures.
- Full-Scale Simulations: A complete failover to the secondary site, mimicking a real disaster as closely as possible. While disruptive and costly, it is the only method to definitively validate that RTO and RPO targets can be met under pressure.
A plan that has never been tested is not a plan—it's a hypothesis. Regular testing turns that hypothesis into a proven, reliable operational asset.
Establishing a Cadence for Review and Updates
Businesses are dynamic; therefore, a DRP cannot be static. The adoption of new software, changes in personnel, and the evolution of operations can all introduce new vulnerabilities or render parts of a plan obsolete.
A fixed review schedule is non-negotiable.
A full plan review should be conducted at least annually. However, certain events should trigger an immediate update, regardless of the annual cycle.
These triggers include:
- Major technology changes, such as migrating to a new cloud provider or implementing a new ERP system.
- Significant operational shifts, like opening a new office or acquiring another company.
- Key personnel changes, particularly within IT or on the designated recovery team.
- After any real-world incident or scheduled test that reveals a deficiency.
This discipline ensures the plan remains aligned with current business reality. A critical component is ensuring communication plans and tools are current. The most robust recovery procedures are useless if you cannot reach your people. Our guide on emergency alert systems for businesses explores the technology that enables effective communication, a critical component of any DRP execution.
Frequently Asked Questions About Disaster Recovery
Even for seasoned risk professionals, the specifics of business disaster recovery planning can raise questions. Here are answers to some of the most common inquiries from decision-makers in commercial insurance and risk management.
What Is the Difference Between Business Continuity and Disaster Recovery?
This distinction is fundamental. Business Continuity (BC) is the overarching strategic framework for maintaining business operations during a crisis. It encompasses people, processes, supply chains, and customer communications.
Disaster Recovery (DR) is a critical subset of business continuity. It is focused specifically on the restoration of IT infrastructure and technology, including servers, networks, data, and applications. In short, DR restores the technology that enables the broader BC plan to succeed.
How Do I Secure Executive Buy-In for DRP Funding?
Securing a budget for disaster recovery requires framing the request in the language of the C-suite: risk and revenue. The Business Impact Analysis (BIA) is your most powerful tool for this.
Avoid asking for funds for "new backup systems." Instead, present the investment as a direct mitigation of a quantifiable financial threat.
For example: "Our BIA indicates that a 48-hour outage of our claims processing system will result in $1.2 million in direct revenue loss and a 10% increase in customer churn. This $150,000 investment in a failover system directly mitigates that catastrophic financial risk." When you connect the expenditure to a specific, material outcome, the conversation shifts from cost to investment.
What Are the First Steps for a Small Business?
For smaller enterprises, developing a comprehensive disaster recovery plan can seem daunting. The key is to start with a focused approach on the most critical elements.
- Identify Critical Functions: Determine the one or two processes absolutely essential for survival. This might be your billing system or your customer database. Focus initial efforts there.
- Implement Robust Data Backup: Before anything else, establish a reliable, automated cloud backup solution for all critical business data. This is often the most cost-effective and impactful first step.
- Develop a Communication Plan: Define how you will contact employees and key clients if standard systems are unavailable. A simple, documented call tree or a designated group chat can be highly effective.
You do not need a perfect, 100-page plan on day one. A simple, tested plan that addresses your greatest vulnerabilities is infinitely more valuable than a complex plan that remains incomplete. Focus on steady, incremental progress. Your DRP can mature as your business grows.
The increasing frequency of severe weather events amplifies the urgency of proactive planning, a point detailed in our analysis of climate change business impact. This reality can be a powerful lever when justifying recovery investments to leadership.
When a disaster occurs, access to real-time intelligence is critical. Insurtech.bpcorp.eu provides Sentinel Shield, a business intelligence platform that helps insurance providers, brokers, and recovery firms convert climate crises into measurable growth opportunities. Access high-intent corporate leads at their moment of greatest need by visiting https://insurtech.bpcorp.eu to learn more.